|
Getting your Trinity Audio player ready...
|

Staying ahead in the rapidly changing world of cybersecurity can be tough. Organizations need to sift through massive amounts of data and react to threats swiftly and efficiently. Managing a company’s security measures is no easy task.
This is where Microsoft Security Copilot steps in. Powered by generative AI, Microsoft Security Copilot is a cutting-edge security solution that delivers customized insights, empowering your team to protect your network more effectively. It integrates seamlessly with other Microsoft security tools and utilizes natural language processing to generate personalized guidance and recommendations.
In this article, we’ll dive into what Microsoft Security Copilot is, explore its advantages, and help you determine whether it’s the right choice to bolster your digital security.
What is Microsoft Security Copilot?
Microsoft Security Copilot is an innovative cybersecurity tool that leverages AI and machine learning to enhance threat detection and response efforts. Its primary goal is to improve the efficiency and effectiveness of cybersecurity operations.
Security Copilot assists security teams by enabling them to:
- Respond to cyber threats
- Process vast amounts of signals
- Assess risks at the speed of machines
Additionally, it integrates with other Microsoft security products and utilizes natural language processing, allowing users to ask questions in plain language and receive customized guidance and insights.
Security Copilot is versatile and can support a range of activities, including:
- Incident response
- Threat hunting
- Intelligence gathering
- Security posture management
- Providing executive summaries on security investigations
How Does Microsoft Security Copilot Work?
Microsoft Security Copilot can be accessed as a standalone tool or through embedded experiences within other Microsoft security products.
Some of the tools that Copilot integrates with include:
- Microsoft Sentinel
- Microsoft Defender XDR
- Microsoft Intune
- Microsoft Defender Threat Intelligence
- Microsoft Entra
- Microsoft Purview
- Microsoft Defender External Attack Surface Management
- Microsoft Defender for Cloud
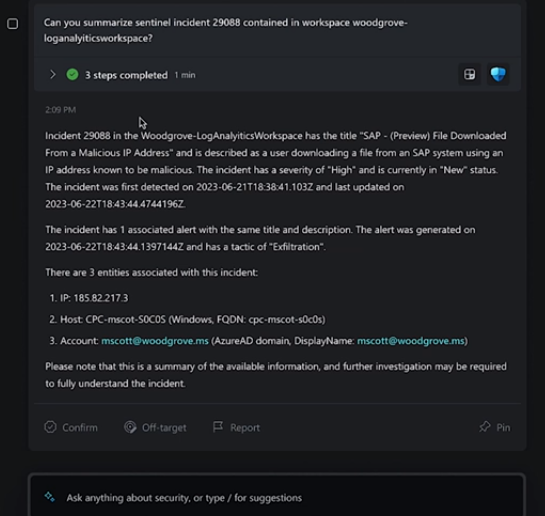
With natural language prompts, using Security Copilot becomes intuitive. You can request information or guidance on various security matters, such as:
- Best practices for securing Azure workloads
- The impact of a specific CVE (Common Vulnerabilities and Exposures) on your organization
- A report on the latest attack campaigns
- Steps to remediate an incident involving specific malware like TrickBot
Should You Consider Microsoft Security Copilot?
Advantages:
1. Enhanced Threat Detection: Security Copilot employs sophisticated algorithms that identify and analyze threats often missed by traditional security measures. Its real-time adaptability to new threats strengthens an organization’s security posture.
2. Operational Efficiency: By automating threat analysis, Copilot allows security teams to focus on strategic decisions. This reduces the time and effort required for manual data analysis and streamlines workflows, leading to quicker threat responses.
3. Seamless Integration with Microsoft Products: Security Copilot works smoothly with a wide range of Microsoft products, creating a cohesive cybersecurity ecosystem. This synergy improves threat visibility and response capabilities.
4. Continuous Learning: The AI and machine learning components of Copilot continuously evolve by learning from new data. This adaptive approach ensures the tool remains effective in combating emerging threats as they develop.
5. Minimized False Positives: Copilot’s advanced algorithms provide more accurate threat detection, reducing the number of false positives that can overwhelm security teams. This leads to a more targeted and efficient response to real threats.
Considerations:
1. Integration Complexities: While Security Copilot integrates effortlessly with Microsoft products, organizations with a diverse array of cybersecurity tools may face challenges. Ensure compatibility with your current cybersecurity infrastructure.
2. Resource Demands: Deploying advanced AI and machine learning technologies might require additional resources. Organizations should verify that their existing infrastructure can support these requirements.
3. Training and Familiarization: To fully benefit from Copilot, proper training and familiarization with its features are necessary. Make sure your security team is well-prepared to maximize the potential of this advanced tool.
Conclusion
Microsoft Security Copilot represents a significant advancement in AI-driven cybersecurity. Its capabilities for real-time threat detection, operational efficiency, and seamless integration make it an attractive option for businesses looking to enhance their digital security.
When considering whether to adopt Microsoft Security Copilot, evaluate your organization’s specific needs, including your existing cybersecurity infrastructure, resource availability, and commitment to ongoing training.
Need Expert Microsoft Support?
Microsoft offers a vast ecosystem of interconnected business tools, and Security Copilot is one of the latest solutions designed to secure your digital environment. If you need help leveraging these tools, we’re here to assist. As experienced Microsoft service providers, we can help you maximize the benefits of these solutions.
Contact us today to schedule a consultation.
Twintel has grown into an expansive, full team of IT services professionals, acting as the outsourced IT department of non-profits, small to mid-size businesses, and enterprise-level corporations in Orange County, across California, and nationally.
Today, it’s the strength and deep expertise of the Twintel team that drives positive outcomes for clients. Each of the support staff, technicians, and engineers works diligently each day to make sure that the companies served have the seamless, secure, and stable IT environments needed to allow them to pursue their organizational objectives.